Published: June 2025
By: Zabel Iqbal, your favourite tech fixer
Estimated Read Time: 6 mins
Category: Cybersecurity, Vulnerability Breakdown
⚠️ TL;DR
Microsoft just patched a nasty bug in Windows that lets attackers go from authenticated user to SYSTEM using SMB and some clever Kerberos trickery. If you’re not enforcing SMB signing, you’re asking for trouble.
Patch your systems. Now.
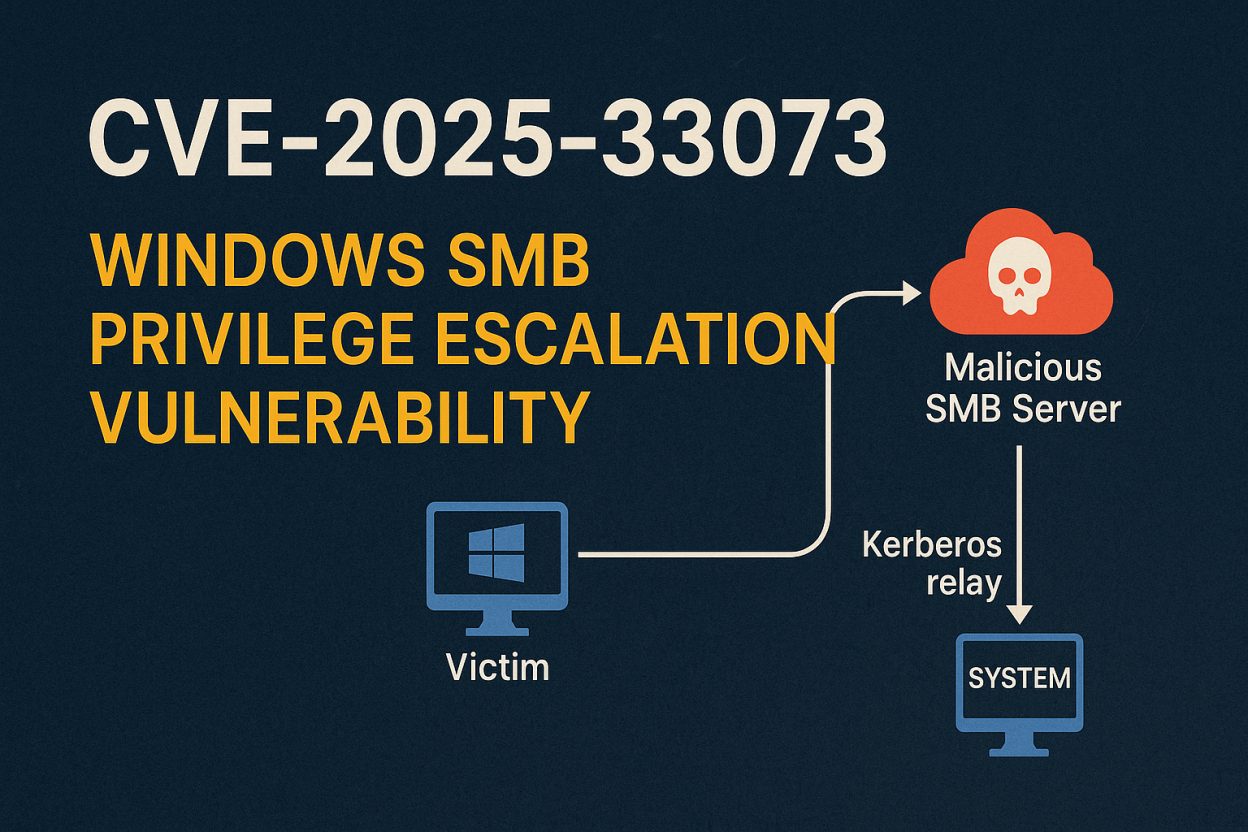
🕳️ What Is CVE-2025-33073?
CVE-2025-33073 is a privilege escalation vulnerability in the Windows SMB client, discovered and responsibly disclosed by researchers at Synacktiv and RedTeam Pentesting.
It abuses a loophole in how Windows handles coerced authentication via SMB. By crafting a malicious authentication exchange, attackers can trick the system into handing them SYSTEM-level access.
And no, this isn’t just a theoretical problem. There’s already a working proof-of-concept (PoC) in the wild.
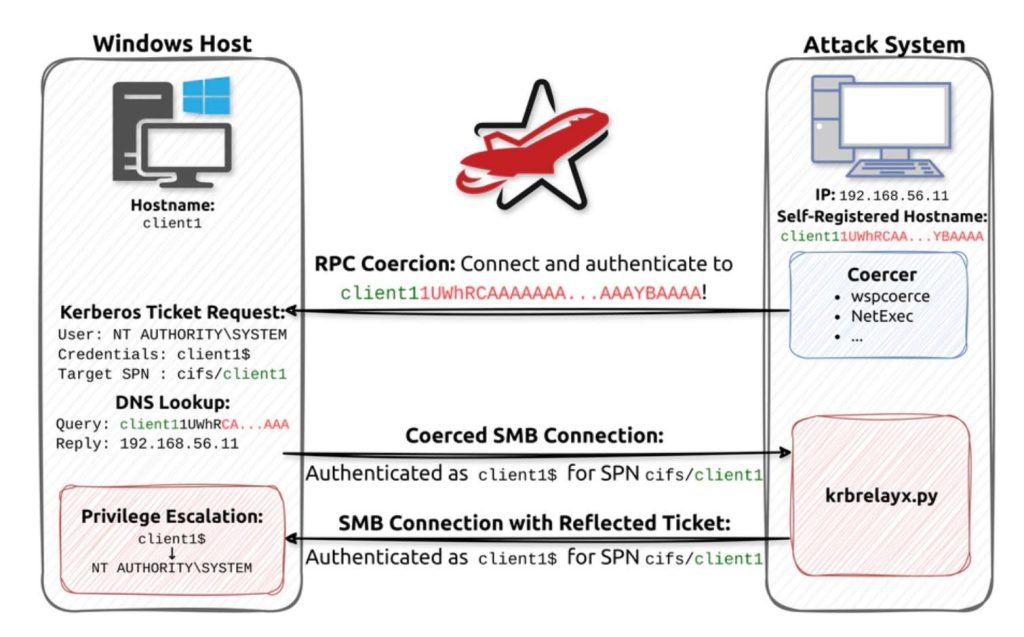
🧠 The Vulnerability Explained (Without Boring You)
Let’s simplify it:
-
The Setup: You (the attacker) convince a Windows machine to connect to your malicious SMB server.
-
The Coercion: The victim machine tries to authenticate to your trap, using either NTLM or Kerberos.
-
The Magic: You relay that authentication attempt right back to the victim machine, in a twisted “Hello, it’s me, trust me” maneuver.
-
The Win: The victim machine believes it’s authenticating itself — and boom, you get a SYSTEM token.
The vulnerability exploits a gap in how lsass.exe marshals target information when interacting with the SMB client, especially in cross-protocol reflection.
📋 Affected Systems
-
Windows 10 (all versions prior to 24H2)
-
Windows 11 (up to 23H2)
-
Windows Server 2019 / 2022 / 2025
If SMB signing is not enforced, you’re vulnerable.
🔐 Real-World Exploitation Example
Imagine this:
-
You send a phishing email with a link to an SMB share.
-
The user clicks it. Their Windows client authenticates to the share.
-
Your malicious SMB service takes that authentication data and reflects it back to their own machine via another vector (like RPC or WinRM).
-
You now have SYSTEM privileges.
This isn’t some deep-zero-day wizardry. It’s practical, scriptable, and has already been demoed at conferences.
🛠 Fix Status
Microsoft released a patch on June 10, 2025, during their regular Patch Tuesday rollout. The fix modifies mrxsmb.sys to validate marshaled target information more strictly and blocks authentication reflection at the kernel level.
You’ll find this under:
-
Windows Updates > KB5037509 / KB5037510 / KB5037512 (depending on your OS version)
🧯 Mitigation Plan (Even if You Can’t Patch Right Away)
Until you can deploy the update, do the following:
✅ 1. Enforce SMB Signing
Prevents attackers from relaying coerced authentication. Use Group Policy or PowerShell:
Set-SmbServerConfiguration -EnableSecuritySignature $true -Force
Set-SmbClientConfiguration -RequireSecuritySignature $true
🔥 2. Block Outbound SMB
Seriously, just block it. Your users don’t need to talk SMB outside your network.
🔍 3. Monitor for Strange Auth Flows
Look for internal machines initiating authentication requests to other internal resources they normally wouldn’t touch.
🧠 Why This Matters (And Why It’s Clever)
This CVE is a perfect example of “old tricks, new clothes.”
Kerberos and NTLM relay attacks have been around for years. But CVE-2025-33073 shows that even in 2025, Windows still has exploitable cracks between subsystems that trust each other a bit too much.
This attack doesn’t require brute force or unpatched Internet-facing services — just a bit of network mischief and a blind spot in trust assumptions.
🚧 Final Thoughts: Don’t Sleep on SMB Bugs
If you manage a Windows fleet and you’re still brushing off Patch Tuesdays or haven’t enforced SMB signing, you’re gambling with ransomware.
Patch. Harden. Monitor. And repeat.
📎 Meta Info
-
CVE: CVE-2025-33073
-
CVSS Score: 8.8 (High)
-
Exploitability: High in enterprise networks
-
Patch Date: June 10, 2025
📥 Want to Automate Detection?
This script scans the Security Event Log for Event ID 4624 (Logon) with Logon Type 3 (network logon) and flags those using NTLM or Kerberos from internal hosts, especially targeting localhost or suspicious internal destinations.
$events = Get-WinEvent -FilterHashtable @{
LogName = 'Security';
Id = 4624;
StartTime = (Get-Date).AddDays(-1)
}
foreach ($event in $events) {
$xml = [xml]$event.ToXml()
$logonType = $xml.Event.EventData.Data | Where-Object { $_.Name -eq 'LogonType' } | Select-Object -ExpandProperty '#text'
$authPkg = $xml.Event.EventData.Data | Where-Object { $_.Name -eq 'AuthenticationPackageName' } | Select-Object -ExpandProperty '#text'
$sourceIP = $xml.Event.EventData.Data | Where-Object { $_.Name -eq 'IpAddress' } | Select-Object -ExpandProperty '#text'
if ($logonType -eq 3 -and ($authPkg -eq "NTLM" -or $authPkg -eq "Kerberos")) {
if ($sourceIP -like "127.*" -or $sourceIP -like "localhost" -or $sourceIP -like "192.168.*" -or $sourceIP -like "10.*") {
Write-Output "Suspicious Network Logon: $($event.TimeCreated) | Source IP: $sourceIP | Auth: $authPkg"
}
}
}
You can modify this to send alerts or pipe into a SIEM.
🧩 Sysmon Configuration (Sysmon + Sigma Rule Inspired)
This rule detects internal SMB traffic to localhost or loopback SMB reflection — which is the core of this exploit.
👉 Sysmon Rule Snippet (XML):
<RuleGroup name="SMB Reflection Detection" groupRelation="or">
<NetworkConnect onmatch="include">
<DestinationIsIpv6>false</DestinationIsIpv6>
<DestinationIp>127.0.0.1</DestinationIp>
<DestinationPort>445</DestinationPort>
<Protocol>tcp</Protocol>
</NetworkConnect>
</RuleGroup>
Add this inside your existing Sysmon config under <EventFiltering>.
🧠 Optional Enrichment:
Also include Event IDs:
-
3 – Network Connection
-
10 – ProcessAccess (e.g., suspicious processes accessing
lsass.exe) -
11 – FileCreate (watch for dropped tools like
ntlmrelayx.pyormimikatz)
🔔 Bonus: Sigma Rule (for SIEM like Splunk, ELK)
title: SMB Reflection Authentication Attempt
logsource:
product: windows
service: sysmon
category: network_connection
detection:
selection:
DestinationIp: 127.0.0.1
DestinationPort: 445
Protocol: tcp
condition: selection
level: high
tags:
- attack.t1557.001
- cve.2025-33073
🚨 Recommendations:
-
Enable Sysmon across endpoints.
-
Log all SMB/NTLM connections.
-
Create an alert if any authenticated session to
127.0.0.1:445happens with SYSTEM token. -
Watch for internal machines suddenly authenticating to each other without prior history.